The given method is applied to attack to block code numbers. Possesses considerably smaller labour input in comparison with a method of full search.
Entry conditions. Are given opened and шифрованный texts. Криптосистема consists from h enciphering cycles. Cyclic keys are independent and have no general bits. Key K of system represents a combination from h-cyclic keys k1, k2... kh (fig. see) 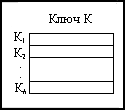
Problem. At known opened and шифрованном texts to find key K.
Let's designate algorithm transformation as Ek (a) =b, where a-clear text, and b-shifrotekst. It is possible to present it as composition Ek1Ek2. Ekh (a) =b, where Eki - cyclic transformation on a key ki. Each key ki represents a binary vector of length n, and the general key of system - a vector of length n*h.
1. Memory filling.
Let's touch all values k ' = (k1, k2. kr), т.е the first r cyclic keys. On each such key k ' we cipher a clear text a - Ek ' (a) =Ek1Ek2. Ekr (a) =S (i.e. it is passable r cycles of enciphering instead of h). We will consider S as a certain address of memory and to this address we will write down value k '. It is necessary to touch all values k '.
2. Key definition.
We touch all possible k "= (kr+1, kr+2... kh). On received keys it is deciphered шифротекст b - E-1k" (b) =E-1kh. E-1kr+1 (b) =S'. If about S' it is not empty, we get therefrom a key k ' and the candidate for keys (k ', k ") =k is received.
However it is necessary to notice that the first received candidate k not necessarily is a true key. Yes, for the given island т an and ш.т.b it is carried out Ek (a) =b, but on other values of a clear text a ' шифротекста b ', received of a ' on a true key, equality can be broken. All depends on concrete characteristics криптосистемы. But sometimes happens to receive such "pseudo-equivalent" key enough. In an opposite case after end of procedures a certain set of keys {k ', k "will be received...} among which there is a true key.
If to consider concrete application шифротекст and a clear text can be great volume (for example, graphic files) and to represent enough great number of blocks for the block code number. In this case for process acceleration it is possible to cipher and decipher all text but only its first block (that much faster) and then, having received set of candidates, to search in it for a true key, checking it on other blocks. To discuss at a forum╗
|