|
That the information has value, people have realised very much for a long time - not without reason correspondence of the mighty of this world long since was object of steadfast attention of their foes and friends. Then there was a problem of protection of this correspondence from excessively curious eyes. Ancient tried to use for the decision of this problem the diversified methods, and one of them was тайнопись - ability to make the message so that its sense was inaccessible to anybody except let into a secret. There are certificates to that art тайнописи has arisen still in доантичные times. Throughout all centuries-old history, up to absolutely recent time, this art served the little, basically to a society top, without falling outside the limits residences of heads of the states, embassies and - is final - prospecting missions. And several decades ago all has changed radically - the information has got independent commercial value and became widespread, almost usual goods. It make, store, transport, sell and buy, so - steal and forge - and, hence, it is necessary for protecting. The modern society all in a greater degree becomes information-caused, the success of any kind of activity all depends on possession certain data and from their absence at competitors more strongly. And the the specified effect, the more potential losses from abusings in information sphere is more strongly shown, and the it is more requirement for information protection.
Among all spectrum of methods of protection of the data from undesirable access the special place is occupied with cryptographic methods. Unlike other methods, they lean only against properties of the information and do not use property of its material carriers, feature of knots of its processing, transfer and storage.
Distinguish two basic methods of enciphering: symmetric and asymmetric.
Symmetric method of enciphering
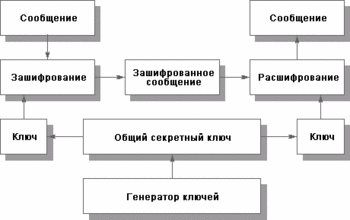 Fig. 1. Use of a symmetric method of enciphering
Fig. 1. Use of a symmetric method of enciphering The same key (stored in a secret) is used both for зашифрования, and for расшифрования the data. Are developed rather effective (fast and reliable) methods of symmetric enciphering. There is also a national standard on similar methods - GOST 28147-89 "Systems of processing of the information. Protection cryptographic. Algorithm of cryptographic transformation".
The Fig. 1 illustrates use of symmetric enciphering. For definiteness we will talk about protection of messages though events can develop not only in space, but also in time when not moving files are ciphered and deciphered anywhere.
The basic lack of symmetric enciphering is that the confidential key should be known both to the sender, and the addressee. On the one hand, it creates a new problem of distribution of keys. On the other hand, the addressee on the basis of presence of the ciphered and deciphered message cannot prove that it has received this message from the concrete sender as it could generate the same message independently.
Assimmetrichnyj method of enciphering
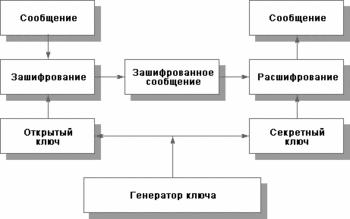 Fig. 2. Use of an asymmetric method of enciphering
Fig. 2. Use of an asymmetric method of enciphering In asymmetric methods two keys are used. One of them, unclassified (it can be published together with other open data on the user), is applied to enciphering, another (confidential, known only to the addressee) - for расшифрования. Most popular of asymmetric is method RSA (Rajvest, Shamir, Adleman), based on operations with big (we will tell, 100-unit) simple numbers and their products.
Let's illustrate use of asymmetric enciphering.
Essential lack of asymmetric methods of enciphering is their low speed, therefore the given methods it is necessary to combine with symmetric (asymmetric methods on 3 - 4 order more slowly). So, for the decision of a problem of effective enciphering with transfer of the confidential key used by the sender, the message at first symmetrically cipher a casual key, then this key cipher an open asymmetric key of the addressee then the message and a key go on a network.
The Fig. 3 illustrates the effective enciphering realised by a combination of symmetric and asymmetric methods.
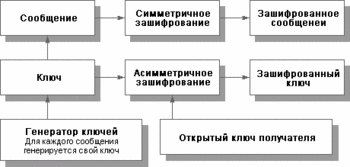 Fig. 3 Effective enciphering of the message
Fig. 3 Effective enciphering of the message On fig. 4 it is shown расшифрование effectively ciphered message.
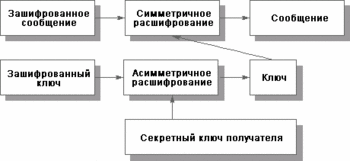 Fig. of 4 Rasshifrovanie of effectively ciphered message
Fig. of 4 Rasshifrovanie of effectively ciphered message Certain distribution was received by a version of the symmetric enciphering based on use of compound keys. The idea consists that the confidential key shares on two parts stored separately. Each part in itself does not allow to execute расшифрование. If law enforcement bodies have suspicions concerning the person using some key, they can receive when due hereunder halves of a key and further operate usual for symmetric расшифрования in the image.
Operating procedure with compound keys - a good example of following to a principle of division of duties. He allows to combine the rights to any secrets (personal, commercial) with possibility effectively to watch infringers of the law though, of course, here it is a lot of subtleties both technical, and the legal plan.
Many cryptographic algorithms as one of parametres demand pseudo-casual value in case of which predictability in algorithm there is a vulnerability (a similar weak spot it was revealed in some variants of Web-navigators). Generation of pseudo-casual sequences - a cryptography prominent aspect on which we will not stop, however.
|
|